The world of IoT is evolving rapidly, changing the way we interact with people, devices and infrastructure. The growth in the number of connected IoT devices is unprecedented and is expected to exceed 50 billion by the end of 2021. Data is the new oil in terms of value, but also because of its attractiveness for crime and interception. According to numerous security experts, cybercrime brought in more than USD 1.5 trillion in 2018. Cybersecurity threats will inevitably become more relevant and dangerous as the number of connected devices increases.
Security is a priority for Capestone and of its long-time partner Teltonika Networks. The Remote Management System (RMS) is no exception. RMS is a cloud-based platform used daily by thousands of companies around the world to easily maintain control of their mission-critical network infrastructure. We would like to give you more information about the steps taken by Teltonika to ensure that RMS users are protected from cyber attacks and unauthorized access.
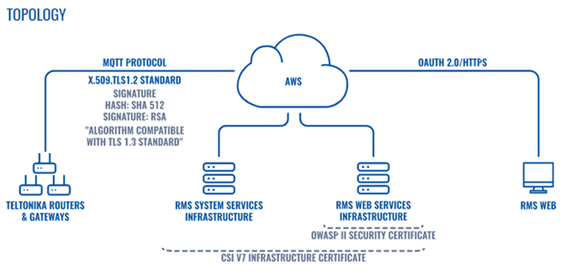
Routers & Gateways from Teltonika Networks communicate with the RMS platform using the Message Queuing Telemetry Transport (MQTT) protocol, which was chosen for its security features. MQTT is secured with a TLS protocol that is secured according to the X.509 TLS 1.2 Standard signature algorithm. All communication between the device and RMS is hashed and signed with RSA signature. Combined, this interaction method meets TLS 1.3 protocol requirements, providing unmatched privacy and performance compared to previous versions of TLS and non-secure HTTP.
All users of Teltonika’s Remote Management system access it via HTTPS; therefore, all communications are encrypted so that no one can intercept your login credentials and gain unauthorized access to the client’s account. To make access even more secure, Teltonika has implemented the OAuth 2.0 authentication method with two-way authentication that prevents unauthorized access even in the event that your login information is misused.
All servers running RMS are hosted by AWS. RMS is CIS v7 infrastructure security certificate compliant, developed to align with the latest cyber threat data and reflect today’s current threat environment. In addition, RMS was tested according to the OWASP methodology by Bell Canada Cyber Security Team, which stated that the security posture of Teltonika Networks’ RMS web application was good, with no vulnerabilities identified.
Manufacturing facilities usually have several complicated specialized machines and equipment that require trained technicians to take care of. These machines are often supplied by different suppliers. If a component stops functioning as it should, this can cause problems for the entire production line which can have a major impact on delays and additional costs.
Furthermore, the recent global pandemic has shown that in no time at all, a large number of workers can be temporarily unavailable due to isolation requirements. In such a situation, remote management becomes essential. Therefore, it is a must to connect professional industrial network equipment to a network and manage it remotely, ensuring the security and reliability of the Internet connection.
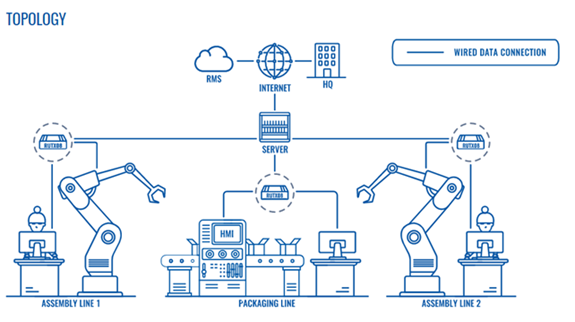
One of the biggest advantages of connecting production machines to the network is the ability to collect data. For example, the RUTX08 router has four Gigabit Ethernet ports with speeds up to 1000 Mbps, digital input/output for remote monitoring and control, and USB 2.0 interface to easily connect the various devices and computers to the Internet. A pre-configured firewall ensures the security of the solution from the start and multiple best rated VPNs provide data encryption.
In addition, a wide interval of supported power supply voltages makes this product suitable for a wide range of electronic devices.
The rugged industrial design with a wide range of tolerated temperatures and vibration resistance makes this device durable and easily applicable in different environments. Add the Management System (RMS) to remotely access the router for updates and maintenance. With RMS Connect, you can do the same with the machines behind the router. This means no technician needs to be present in a production facility to configure, troubleshoot and manage the equipment. It is also possible to set up event-based reporting; for example, an email is sent after a specific event occurs which is defined in pre-configured rules.






